beelzebub
Basic Information
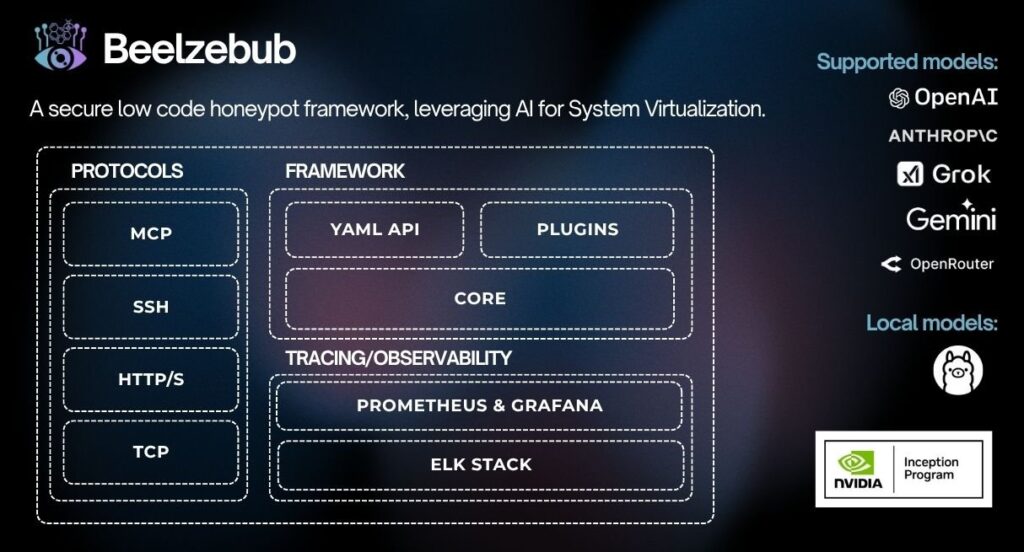
Beelzebub is an advanced, low-code honeypot framework for detecting and analyzing cyber attacks. It uses AI-driven LLM integrations to convincingly simulate high-interaction systems while retaining a low-interaction architecture for safety and manageability. The project is intended for security teams and researchers who need realistic decoy services and automated collection of attacker behavior. Configuration is YAML-based and modular so operators can define services and ports per file. The repository includes example configurations for SSH, HTTP, TCP and a specialized MCP protocol that monitors prompt-injection attempts against LLM agents. Beelzebub is container and orchestration friendly with Docker Compose, Docker images, a Helm chart for Kubernetes, and examples to run the binary built with Go. It also provides observability hooks and guidance for logging and integration with common stacks.